
Holding up a supermarket or a gas station can pay off for criminals. Retailers are a worthwhile target, especially at night when the day’s takings are still at the store. But the potential yield for cyber criminals is far greater. While retailers for decades had plenty of time to prevent shoplifting in their stores, IT security has not been a real issue in the industry sector for quite some time.
It still applies to most retailers today: stores are extensively equipped with video surveillance and electronic tags but when it comes to “data security“, retailers just shake their heads. In the EHI study ”IT Trends in Retail 2015“ , only nine percent of participating retailers mentioned the subject of IT security when asked about the latest technology trends.
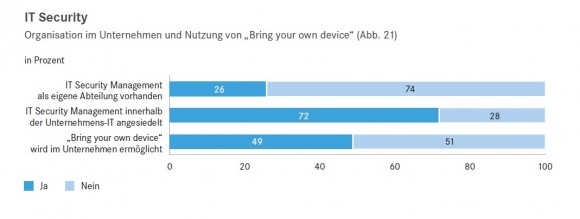
Even though at least 26 percent of interviewed companies have a designated department to handle IT security management, it is still often possible for somewhat experienced hackers to steal thousands or millions of credit card and customer information without any major effort and make large profits by selling it. They gain access using various methods such as viruses, spyware or phishing (a method to acquire personal information of a user by setting up fake websites or emails). They gain access to the retailer’s network and are able to steal sensitive data.
Major retail chains are primary targets
By nature, networks of major retailers are especially complex and include various components like the internal network management, geographical markets, stores, POS systems, sales assistants, suppliers, customers and mobile devices. The larger the retailer, the more customers he has. The data trove criminals need to break into is subsequently also huge for multinational corporations. Last year, the Dell computer company published a list of the most serious attacks to date on major retail chains (though only those cases affecting the U.S.).
Beyond the United States borders, for example, the theft of 40 million credit and debit card numbers and other personal data of 70 million customers of U.S. discount retailer Target made headlines. It still is the largest case of data theft in U.S. retail. Home Depot (56 million stolen credit card numbers and 53 million exposed email addresses) as well as Michaels (three million stolen credit and debit card numbers) are also among the most prominent victims.
Cyberattacks are on the rise – digitization is also to blame
In a recent survey by Capgemini Consulting, 44 percent of all companies in the “consumer goods & retail” industry indicated to have been a victim of a cyberattack at least once. Especially the advancing digitization in stores with new services like free Wi-Fi for customers or digital in-store services such as QR codes and navigation apps create new risks. In the case of insufficient security, these can also represent entry points for cyber criminals.
To get to know their customers better, retailers store far more personal data than they used to in the past – everything ranging from customer purchase history to detailed profiles primarily generated with the use of loyalty programs. And needless to say, the increasing amount of data also increases the incentive to steal it.
Serious repercussions for retail companies
Many retailers are actually oblivious to the consequences of data theft on a grand scale, which is why they also underestimate the required investment or even completely forego security solutions. Cyber criminals obviously don’t steal any tangible assets (such as cash for example). However, they potentially wreak even more havoc through data theft. After all, when serious cases of data breaches become public, retailers need to invest significantly in communications with their customers.
In the months immediately following the theft of customer information, Target, for example, invested a whopping 61 million U.S dollars in customer communication to put its concerned customers at ease. Added to this are potential payments resulting from the retailer’s promise to its customers to pay any fraudulent charges that can be directly traced back to the data breach. All of this resulted in Target’s profit falling 46 percent during the subsequent Christmas season. Other retailers like Staples for instance even offered its potentially vulnerable customers to bear the costs for identity theft protection – for example, credit monitoring services or free credit reports.

Added to this is the fact that digital theft is harder to quantify and measure than the loss of cash for example. What’s more, hackers might have stolen or copied more data than it first appears. At the same time, there is always a risk that previously undetected malware remained in the network and might lead to further losses at a later point in time.
Centralized threat assessment – segmentation of network resources
In the case of a typical data leak in retail, data collected at the POS is shifted to other parts of the network where it actually does not belong. In a white paper on network security in retail, Dell recommends a zone-based security concept. When retailers split network interfaces such as customer computers, inventory servers and back office databases within the network into separate zones, it is easier to ensure that only authorized users have access to the respective zones. In this case it would mean that data from the POS is only forwarded to payment processing, but data transmission to other areas of the network would effectively be impossible.
This is certainly an effective method to quickly detect unauthorized data transfer, or ideally to prevent it entirely. However, consolidating data is just as important. When information about various network threats is consolidated in the cloud, the available computing power is simply higher, which in turn results in shorter response times and enables a more effective defense against security threats.
The key to effectively protecting a retail network, on the one hand, lies in segmentation to quickly identify unauthorized data transfers. On the other hand, information on network threats needs to be synchronized in the entire company, so that you can take action against the attack on a broad scale.









